What is a Hardware Security Module (HSM)?

A Hardware Security Module, or HSM, is a physical hardware module designed to store and process cryptographic keys, making them accessible to authorized users. The primary goal of HSM is to enable employees to use private keys without granting them direct access. This is a security that reduces the attack surface for financial systems, transactions, and enterprise apps.
HSM looks like a PCIe card or a small network appliance, connecting to the motherboard or installed over the network to protect encryption keys.
At ServerMania, we’ve been focusing on keeping customers’ information secure since 2002. We use HSMs in our secure infrastructure deployments across our dedicated servers and AraCloud cloud servers. Together, these platforms allow you to deploy HSM-backed security without sacrificing performance or server control.
In this guide, you’ll learn how HSM works, whether you need it, and what protection matters the most when it comes to data security.
What is a Hardware Security Module (HSM)?
As mentioned, an HSM or (Hardware Security Module) is a real and physical piece of hardware that is designed to generate, store, and later use cryptographic keys. These keys are used after an authorized user needs to sign in, authenticate, use a certificate, or provide a digital signature.
This empowers authorized users to perform management-level functions and tasks without the risks of having access to critical firm information.
The main reason for HSM’s development is, of course, security.
Unlike software key stores, an HSM never exposes private keys to the operating system. Keys stay inside the device. Cryptographic operations happen inside the hardware. The server sends a request such as “sign this data” or “decrypt this value,” and the HSM returns only the result.
HSMs include three primary layers of protection:
| 1. | Tempering Resistance | As soon as the HSM device detects any physical temper like probing or a voltage change, it immediately deletes all keys. |
| 2. | Secure Key Generation | The keys are being created based on secure random number generators; therefore, no guessing can be involved. |
| 3. | Strict Access Control | The authorization works by recognizing administrator roles and application authentication, even on a root-access level. |
In real systems, HSMs handle requests such as:
- Stores and safeguards SSL and TLS private keys.
- Securing payment transactions & PIN processing.
- Securely signing software updates and containers.
- Managing encryption keys for databases/backups.
- Securely running a private certificate for authority.
That’s only the tip, of course. HSM has so many applications that if we were to list them all, it would take days to read through all of them. However, more for HSM’s applications a bit later.
Now, let’s learn…
How Does HSM Work?
An HSM works separately as a secondary processor, or call it a second “brain” if you want, with the sole purpose of verifying requests. The idea is simple. Applications don’t think, so when they identify a sensitive operation, they send it to the isolated HSM module, the execution happens inside the HSM, and the user only receives the final output.
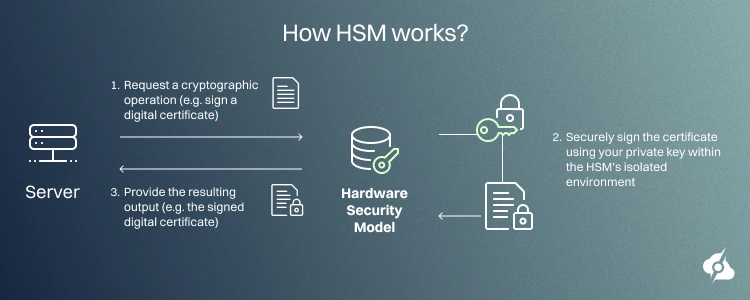
If this sounds too complicated, don’t worry, we’re breaking it down into steps. Please refer to the image below to understand the three critical steps that shape the operation of an HSM process.
See Also: Top 5 Ways to Secure Your Linux Server
Step 1: Server Requests a Cryptographic Operation
It all starts within the application that relies on HSM.
When a service requires decrypting something, generating a key, or signing data using critical company information, it opens a session with the HSM module. It uses interfaces like PKCS#11, Microsoft CNG, and Java JCE.
This is when the user authentication happens.
It works by verifying the user’s cryptographic credentials, whether they are on a disk, flash drive, or other token, typically physically connected to the server. The request is sent to the HSM with strict parameters describing the operation. The application never receives the company data, as the full operation happens within the HSM; this is even beyond the reach of the server system.
Naturally, the HSM requires access rules before processing anything. So, when the validation is successful, the output is returned to the application.
Typical operations requested at this stage:
- Digital signing
- Data decryption
- Key generation
Here’s the complete request flow overview:
| Component: | Action: | Security Purpose: |
| Application | Sends an authenticated request. | Prevents anonymous access. |
| Client Library | Encrypts the communication. | Protects the data in transit. |
| HSM Policy | Validates role and key rules. | Blocks unauthorized use. |
| HSM Scheduler | Queues approved operation. | Controls resource access. |
This gatekeeping guarantees that only approved workloads reach the HSM cryptographic core.
See Also: Network Switch Security 101
Step 2: HSM Operation Inside Isolated Hardware
After the authorization process, the HSM handles the processing internally. As mentioned, this is beyond even the operating system’s reach. The HSM uses the dedicated cryptographic CPU to perform the calculations (not the server’s CPU). This means that without authorization, even the system administrators can’t access or read the data.
The execution stage also has multiple layers of defense. This is the most protected stage, and the HSM monitors voltage levels, stability, temperature, and physical intrusion attempts.
Abnormal conditions trigger immediate zeroization, which deletes all keys from memory.
For signing, the HSM hashes the input data and signs the hash using the internal private key. For decryption, the encrypted data is processed internally and converted to plaintext without exposing intermediate states.
All actions generate audit records stored in protected logs. These logs support the compliance audits and forensic analysis.
Here is the internal execution model:
| Layer: | Role: |
| Secure Key Storage | This layer holds encrypted private keys. |
| Cryptographic Engine | Executes RSA, ECC, AES, and hashing. |
| HW Tamper Detection | This layer triggers the key destruction. |
| Policy Enforcement | This layer fully enforces key usage rules. |
| Audit System Logs | The audit layer records all sensitive events. |
It’s a system designed to protect your data on all levels!
See Also: How to Restrict Access to IPs for Network Security
Step 3: HSM Returns the Result to the Server
Once processing finishes, the HSM releases only the final output.
Depending on the request, this output could represent a digital signature, decrypted data block, verification status, or newly generated public key. So, the private key remains sealed inside the device. The server then continues normal execution.
For instance:
- A web server attaches a signature to a TLS handshake.
- The payment processor forwards the signed transaction.
- A database service stores decrypted records in memory.
From a developer’s perspective, the call resembles a standard cryptographic function. From a security perspective, the difference is fundamental.
The most sensitive assets never enter the system memory space.
💡Quick Example: (Oversimplified)
A company employee needs to sign a PDF document before sending it to the client. However, the employee doesn’t have access to the digital signature of the company. The application used for signing in documents sends a request to the HSM, the HSM recognizes the employee as an authorized user, and signs the document internally.
The employee’s role allows him to only sign specific document types. If the employee tries to sign in a document beyond his role’s scope, the HSM rejects it.
Bottom Line: An ideal layer of protection against internal/external access-inspired attacks!
Do You Need HSM? | Workflow-Based Framework
An HSM surely brings additional costs, operational efforts, and integration work. Therefore, the decision whether you need HSM or not heavily depends on how sensitive the data you deal with is. Here’s a quick workflow-based framework to help you identify how important HSM is for you.
When HSM Is Necessary
HSM is necessary when you deal with systems that handle high-value assets, legal trust, or any other compliance and regulated data. Something that you can’t afford to get exposed to, altered with, or tempered in any way. In short, HSM is needed where a single compromise results in financial loss and penalties.
Here are a few examples:
| Workload: | Why HSM is Necessary: |
| Payment Processing | HSM here is critical for signing and decrypting transactions, which must meet PCI security standards. |
| Certificate Authority | HSM is important here because root and issuing keys must never leave protected hardware. |
| Banking Platforms | HSM keys are used here to secure money movement, transaction data, and customer identities. |
| Multi-Tenant SaaS | HSM is used to store data, and one leaked key could expose data across many customers. |
Note: In many of these cases, HSM is legally mandated.
When HSM Is Recommended
HSM is recommended but not mandatory when you manage production systems and deal with sensitive data containing control access. Here, HSM is not legally required, but not having it can leave your data vulnerable to access-inspired attacks.
Here are a few examples:
| Workload: | Why HSM Helps: |
| Encrypted Databases | HSM protects master encryption keys from system administrators and malware while supporting secure automated decryption. |
| API Authentication Services | HSM secures long-lived signing keys used to issue and validate access tokens across distributed services. |
| Backup Encryption Systems | HSM prevents offline theft of backup keys, which could expose large volumes of archived data. |
| CI/CD Signing Pipelines | HSM blocks unauthorized signing of software releases even if the build servers are compromised. |
Note: It is up to the company to decide whether they want to adopt HSM into their workflow.
When HSM Is Not Needed
HSM is not required when you run low-risk systems with limited data sensitivity, small teams, and short-lived keys. Your workflows involve minimal automation and fast recovery from key rotation, which reduces the impact of compromise.
Here are some examples:
| Workload: | Why Software Security? |
| Development Environments | Test systems use non-sensitive data and rotate keys frequently, which limits the impact of compromise. |
| Internal Tools | Small user groups and restricted access reduce the value of hardware-level key isolation. |
| Short-Lived Web Sessions | Session keys expire quickly and are regenerated often, minimizing long-term exposure risk. |
| Prototypes and Staging | Security models change before production, making hardware key protection unnecessary at this stage. |
So, based on the nature of your workflow, do you need an HSM?
See Also: Understanding IP Address Abuse
What is PCI Compliance?
The PCI Security Standards Council regulates HSM security.
This community shapes, manages, and regulates security measures that must be implemented in a payment environment. It also defines the secure types of algorithms and how many should be used for data encryption and decryption.
Like financial institutions, ServerMania’s infrastructure security is regularly monitored to ensure compliance with international regulatory statutes and industry standards. Our network security is locked down on multiple logical layers using various methods, including private networking.
Secure Your Workflow with ServerMania
If you understand the value of HSMs, but you struggle with deployment, hardware selection, and all the compliance surrounding it, we’re here to help. For over a decade, ServerMania has been helping organizations secure their workflows through HSMs.
We can provide you with the foundation to integrate cryptography into your infrastructure and focus on the importance of your business, not the security.

Why Choose ServerMania
Here’s why securing your workflow with ServerMania makes sense:
- Top-tier dedicated servers with PCIe HSM support
- AraCloud for scalable HSM-backed infrastructures
- Compliance-ready servers for regulated workloads
- Full hardware control, root access, and assistance
- Enterprise-grade data center security & compliance.
💬Contact ServerMania today through our 24/7 customer service or book a free consultation with HSM experts. We’re available right now!
Was this page helpful?

